I mentioned earlier that I am using the Tmobile "myFaves" plan. This plan allows me unlimited calling to five numbers and 300 minutes to all other numbers. Now, there are two, maybe three, people that I talk to regularly so they instantly went into my "faves". For the remaining slots available, I want to make sure that I am getting the numbers in there that I talk to frequently. Since I'm allowed to make changes once per month, I have been going through a quick spreadsheet analysis to determine which numbers I am using the most and ensure they are in my "faves".
To do this analysis, I first downloaded my call records from Tmobile's website. They offer the ability to download in a CSV format making it easy to import into your favorite spreadsheet.
I, then, created a pivot table on my call data. (If your favorite spreadsheet cannot do pivot tables, then get the free OpenOffice application.) To create the pivot table, I simply highlight the data, drag the "minutes" column into the main data space, drag the "numbers" column into the left-hand row space, and click "done".
Once the pivot table has aggregated all my minutes by number, I then highlighted that dataset, sort descending by minutes, and I now have a nice list of my most frequently used numbers!
Using the top five of these numbers, I go back to Tmobile's website (which has timed out my login. Nice.) and "manage" my "faves". This has been a very useful activity taking about 10 minutes once per month. This activity really saved me last month when a friend that is on my list of five changed their phone number. I updated it in my phone's contact list, but did not remember to update my "faves" until just now when I looked at the data. It would be nice if Tmobile would aggregate the data in this way, but I suspect it is not in their interest for me to have a finely tuned "fave" list.
Technology Stuff
Saturday, December 29, 2007
Sunday, December 16, 2007
Local Shared Objects (aka: Flash cookies)
Just when you thought you were protecting your privacy by preventing cookies being stored on your computer, The Man has found another way to do the same thing.
The Man's new trick is called "Local Shared Objects" (LSO). LSO describes the capability of Adobe's Flash software to store information on your computer without you knowing about it. Furthermore, other websites can access this information to understand more about you and places that you have visited before.
Adobe provides a tool to give you control over how LSOs are stored on your computer. I highly suggest that you check this out and alter the default settings for your computer. To use the tool, log onto the Settings Manager, and jump over to the "Website Privacy Settings Panel".
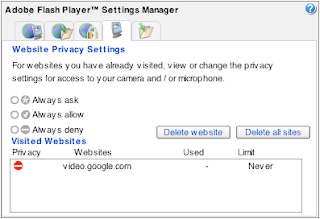
You will likely see a long list of "Visited Websites". As soon as I saw this, I immediately hit the "Delete all sites" button and then thought about taking a picture. Oh well...
Browse through each of the tabs along the top. If you are like me, you will be appalled at some of the default settings. (Why yes, actually, I would like third parties to access my webcam!) For example, the default setting on the "Storage Settings" tab allows every website to store up to 100KB of data on your computer! Move that slider to zero, pronto.
Next, head on over to the "Global Storage Settings Panel" and un-check the option to "Allow third party Flash content to store data on your computer". This is supposed to prevent any future storage of LSOs on your computer. I will be watching mine closely to see how it works.
I supposed we should be grateful that The Man (Adobe, in this case) provides the Settings Manager in the first place. I just wish the defaults for this kind of stuff were in favor of my privacy instead of the other way around.
Oh, and don't forget to load up the Settings Manager on every computer you use. Yes, it is too much to ask to only do it once.
The Man's new trick is called "Local Shared Objects" (LSO). LSO describes the capability of Adobe's Flash software to store information on your computer without you knowing about it. Furthermore, other websites can access this information to understand more about you and places that you have visited before.
Adobe provides a tool to give you control over how LSOs are stored on your computer. I highly suggest that you check this out and alter the default settings for your computer. To use the tool, log onto the Settings Manager, and jump over to the "Website Privacy Settings Panel".

You will likely see a long list of "Visited Websites". As soon as I saw this, I immediately hit the "Delete all sites" button and then thought about taking a picture. Oh well...
Browse through each of the tabs along the top. If you are like me, you will be appalled at some of the default settings. (Why yes, actually, I would like third parties to access my webcam!) For example, the default setting on the "Storage Settings" tab allows every website to store up to 100KB of data on your computer! Move that slider to zero, pronto.
Next, head on over to the "Global Storage Settings Panel" and un-check the option to "Allow third party Flash content to store data on your computer". This is supposed to prevent any future storage of LSOs on your computer. I will be watching mine closely to see how it works.
I supposed we should be grateful that The Man (Adobe, in this case) provides the Settings Manager in the first place. I just wish the defaults for this kind of stuff were in favor of my privacy instead of the other way around.
Oh, and don't forget to load up the Settings Manager on every computer you use. Yes, it is too much to ask to only do it once.
Sunday, November 25, 2007
Take back your email address
How many times a week do you get prompted for an email address while you are surfing the ol' web? Once? Three times? Multiple times a day? It probably depends on what kind of surfing you do, but it seems that every site wants your address these days. They assure you that they won't sell it or rent it to anyone else, and I'll actually giving them the benefit of the doubt that they honor this promise.
Yet, when you hand it over in order to get some free download or other wares, the marketing campaigns begin. I'm not necessarily talking about spam, although that is certainly something to be concerned about. No, I'm referring to the continuing stream of "special deals", coupons, and other crap that companies want to send you.
Here's another scenario that gets to me regularly. I need to purchase a hard to find item. The big stores that I usually do business with don't have it, so I have to Google for a niche website that carries it. While I'm glad to have found the item in question, I now have to give my address. Now, I do want to get things like shipping notices and order confirmations, but I don't want all the stuff that comes after I've received my order.
So, there's the problem. Now, for the solution. To key to preventing someone keeping your address longer then you want them to is to use a disposable address! If the address they have no longer goes to my primary inbox, then I have no problem at all with them keeping it on file for as long as they want. :)
The great folks over at spamgourmet have provided a service that does this. To use this service, you need to create a login and give them your primary email address. (I know, I know... don't worry, this is the last time you need to surrender your "real" address) Once you have a login name, you are ready to go. Next time you are asked to provide an address, you just follow a pattern. The pattern looks like this:
In the pattern above, you would replace the text "label" with a unique string that is meaningful to you. I usually use the name of the company or website that I am filling out. (This gives me the added advantage of knowing if they did sell their email list to another firm.) Next, you replace the text "number" with a number, either numeric or fully spelled out. Finally, you replace the text "login" with the login name that you created when you originally signed up and keep everything else the same. Here is how it might look:
The number in the middle is really the interesting part of all this. Basically, the way that this works is that Best Buy (in my example) will send email to the spamgourmet address. Spamgourmet will then forward the email to my real address if I have received less then 6 messages to the spamgourmet address. Once, I have received 6 messages, then spamgourmet will no longer forward them. They call this "eating" my spam. Next time I actually want to buy something from Best Buy, I login to spamgourmet, search for my bestbuy disposable address, and tell them I want to receive 6 more messages. Easy!
To show how much of an impact this has made for me, I'll publish my stats. These are provided by spamgourmet. "Your message stats: 1,428 forwarded, 18,458 eaten. You have 149 disposable address(es)." This gives me a ratio of almost 13 messages "eaten" for every 1 that I've actually received. Wow...
Oh, and did I mention that spamgourmet is free?
Yet, when you hand it over in order to get some free download or other wares, the marketing campaigns begin. I'm not necessarily talking about spam, although that is certainly something to be concerned about. No, I'm referring to the continuing stream of "special deals", coupons, and other crap that companies want to send you.
Here's another scenario that gets to me regularly. I need to purchase a hard to find item. The big stores that I usually do business with don't have it, so I have to Google for a niche website that carries it. While I'm glad to have found the item in question, I now have to give my address. Now, I do want to get things like shipping notices and order confirmations, but I don't want all the stuff that comes after I've received my order.
So, there's the problem. Now, for the solution. To key to preventing someone keeping your address longer then you want them to is to use a disposable address! If the address they have no longer goes to my primary inbox, then I have no problem at all with them keeping it on file for as long as they want. :)
The great folks over at spamgourmet have provided a service that does this. To use this service, you need to create a login and give them your primary email address. (I know, I know... don't worry, this is the last time you need to surrender your "real" address) Once you have a login name, you are ready to go. Next time you are asked to provide an address, you just follow a pattern. The pattern looks like this:
label.number.login@spamgourmet.com
In the pattern above, you would replace the text "label" with a unique string that is meaningful to you. I usually use the name of the company or website that I am filling out. (This gives me the added advantage of knowing if they did sell their email list to another firm.) Next, you replace the text "number" with a number, either numeric or fully spelled out. Finally, you replace the text "login" with the login name that you created when you originally signed up and keep everything else the same. Here is how it might look:
bestbuy.6.michaelscott@spamgourmet.com
The number in the middle is really the interesting part of all this. Basically, the way that this works is that Best Buy (in my example) will send email to the spamgourmet address. Spamgourmet will then forward the email to my real address if I have received less then 6 messages to the spamgourmet address. Once, I have received 6 messages, then spamgourmet will no longer forward them. They call this "eating" my spam. Next time I actually want to buy something from Best Buy, I login to spamgourmet, search for my bestbuy disposable address, and tell them I want to receive 6 more messages. Easy!
To show how much of an impact this has made for me, I'll publish my stats. These are provided by spamgourmet. "Your message stats: 1,428 forwarded, 18,458 eaten. You have 149 disposable address(es)." This gives me a ratio of almost 13 messages "eaten" for every 1 that I've actually received. Wow...
Oh, and did I mention that spamgourmet is free?
Saturday, October 27, 2007
Upgrade your Wireless Router
Today, I upgraded my wireless router. Not because it was broken, but just because it was there, you know?
When Linksys was its own company, it did a very cool thing. It based some of its devices on the Linux operating system, which made it very easy for enterprising young folks to do the same. Fast forward a few years and now you can take a third party operating system and place it on your Linksys wireless router.
I've been reading about the excellent DD-WRT package for some time now. This afternoon, I found the time to give it a try. (Actually, I was just running out of excuses to do yardwork, and this fit the bill nicely.) In less then an hour, I had downloaded the software, flashed the router, and re-configured it to use my existing SSID and network information. While, it doesn't compete with Apple's 300, it does have quite a few interesting features. It brings a lot of new ideas to the home broadband router area. It can update your DDNS information, host your PPTP VPN session, provide a full SSH management login, and keep its time current with any NTP server. My favorite feature is probably the ability to increase the power of the radio so my devices downstairs can get a better connection.
Anyway, let's just say that I'm impressed. I've even considered using it to replace my custom-built Debian firewall that currently guards my home network. If you want to give it a try, it supports much more then just Linksys, so visit this page to see if your device is supported. If yours isn't and you are ready for an upgrade, you can pick up the very nice Linksys WRT54G for around $50.
When Linksys was its own company, it did a very cool thing. It based some of its devices on the Linux operating system, which made it very easy for enterprising young folks to do the same. Fast forward a few years and now you can take a third party operating system and place it on your Linksys wireless router.
I've been reading about the excellent DD-WRT package for some time now. This afternoon, I found the time to give it a try. (Actually, I was just running out of excuses to do yardwork, and this fit the bill nicely.) In less then an hour, I had downloaded the software, flashed the router, and re-configured it to use my existing SSID and network information. While, it doesn't compete with Apple's 300, it does have quite a few interesting features. It brings a lot of new ideas to the home broadband router area. It can update your DDNS information, host your PPTP VPN session, provide a full SSH management login, and keep its time current with any NTP server. My favorite feature is probably the ability to increase the power of the radio so my devices downstairs can get a better connection.
Anyway, let's just say that I'm impressed. I've even considered using it to replace my custom-built Debian firewall that currently guards my home network. If you want to give it a try, it supports much more then just Linksys, so visit this page to see if your device is supported. If yours isn't and you are ready for an upgrade, you can pick up the very nice Linksys WRT54G for around $50.
Saturday, October 20, 2007
Connect to your home network (SSH)
In my last post, I discussed how I keep track of my home IP address so that I could connect from "outside", whether I'm at my parent's house, traveling, or in a coffee shop.
Now, if you are going to connect from the typical open wireless access that you will find at a coffee shop, then you should be thinking about the security of the information you pass to your home network. It is incredibly easy to eavesdrop on your web session on an open wireless network. There are, as always, multiple ways to connect home securely. I will show you a couple of different ways to do it.
From here on out, this post will reference a Mac system that is connected directly to the Internet without any sort of firewall in the middle. Next week, I'll do a similar post for those of you gutsy enough to connect your Windows system directly to your external connection.
On my home system, I have configured the SSH server to allow traffic from my internet connection. I can then connect to that from a Windows, Mac, or *nix system. When making the SSH connection, I choose the options to allow tunneling. This allows me to then connect to my home system while "tunneling" through the secure SSH connection.
From the Mac system that you are currently sitting at, the command you would use to do this is (all one line):
ssh -L 5931:localhost:5900 username_on_home_system@my_home_system.dyndns.org
By running this command, you are attempting to login to your system at home using an account named "username_on_home_system". Once you authenticate successfully, you instruct SSH to connect port 5931 on the system sitting in front of you to port 5900 on your home system.
Once you have successfully made this connection, then you can use a remote desktop application like RDP (for Windows) or VNC (for Windows, Mac, and lots of other systems). I use VNC on my home system, so that is why I chose the port number 5900 when connecting SSH. To connect to my home system, I use a VNC client like Chicken of the VNC and configure it to connect to the local systems sitting in front of me.

It may seem odd to be trying to connect VNC to the system that you are currently sitting at, but keep in mind that the SSH program is going to forward anything you send to your local port 5931 to the port 5900 on your system at home. If you've done everything correctly, you should be looking at your home desktop, and it will be completely encrypted while doing so! Now, you can launch programs on your home system just as if you were sitting there.
I hope you find this helpful. It can be complicated, but your privacy and security are well worth taking the time to figure it out. If you have questions, leave a comment for me and I'll do my best to help you out.
Now, if you are going to connect from the typical open wireless access that you will find at a coffee shop, then you should be thinking about the security of the information you pass to your home network. It is incredibly easy to eavesdrop on your web session on an open wireless network. There are, as always, multiple ways to connect home securely. I will show you a couple of different ways to do it.
From here on out, this post will reference a Mac system that is connected directly to the Internet without any sort of firewall in the middle. Next week, I'll do a similar post for those of you gutsy enough to connect your Windows system directly to your external connection.
On my home system, I have configured the SSH server to allow traffic from my internet connection. I can then connect to that from a Windows, Mac, or *nix system. When making the SSH connection, I choose the options to allow tunneling. This allows me to then connect to my home system while "tunneling" through the secure SSH connection.
From the Mac system that you are currently sitting at, the command you would use to do this is (all one line):
ssh -L 5931:localhost:5900 username_on_home_system@my_home_system.dyndns.org
By running this command, you are attempting to login to your system at home using an account named "username_on_home_system". Once you authenticate successfully, you instruct SSH to connect port 5931 on the system sitting in front of you to port 5900 on your home system.
Once you have successfully made this connection, then you can use a remote desktop application like RDP (for Windows) or VNC (for Windows, Mac, and lots of other systems). I use VNC on my home system, so that is why I chose the port number 5900 when connecting SSH. To connect to my home system, I use a VNC client like Chicken of the VNC and configure it to connect to the local systems sitting in front of me.

It may seem odd to be trying to connect VNC to the system that you are currently sitting at, but keep in mind that the SSH program is going to forward anything you send to your local port 5931 to the port 5900 on your system at home. If you've done everything correctly, you should be looking at your home desktop, and it will be completely encrypted while doing so! Now, you can launch programs on your home system just as if you were sitting there.
I hope you find this helpful. It can be complicated, but your privacy and security are well worth taking the time to figure it out. If you have questions, leave a comment for me and I'll do my best to help you out.
Sunday, October 14, 2007
Connect to your home network (Dynamic DNS)
Ever been at work or at a friend's house and wanted to log into your home connection? Know the IP address off the top of your head? Well, if you're like me, then you probably don't remember it. Even if you write down your current address, it will likely change on you by the time you need it.
To make this easier, your ISP will assign you a dedicated IP address. This will allow you to always have the same address and make it easier to connect to your home network. Problem is, they will want to charge you a monthly fee for the privilege.
Fortunately, there is a free service available to make it possible to get by without a dedicated address. The concept is called Dynamic DNS and the website that I use that offers this service is called DynDNS.
Basically, the way that this works is that a central party keeps track of your computer's IP address. By downloading a special client to your computer, you can configure it to send an update to DynDNS whenever its address changes. This allows you to use DNS to easily recall the exact address that your home computer is using at any time. DynDNS is easy to setup with the hardest part being choosing which of the 80 domain names that you want to use.
This should allow you to find your home network on the Internet. Next, I'll cover how I securely connect and encrypt all communications to my home network.
Part 2, SSH
To make this easier, your ISP will assign you a dedicated IP address. This will allow you to always have the same address and make it easier to connect to your home network. Problem is, they will want to charge you a monthly fee for the privilege.
Fortunately, there is a free service available to make it possible to get by without a dedicated address. The concept is called Dynamic DNS and the website that I use that offers this service is called DynDNS.
Basically, the way that this works is that a central party keeps track of your computer's IP address. By downloading a special client to your computer, you can configure it to send an update to DynDNS whenever its address changes. This allows you to use DNS to easily recall the exact address that your home computer is using at any time. DynDNS is easy to setup with the hardest part being choosing which of the 80 domain names that you want to use.
This should allow you to find your home network on the Internet. Next, I'll cover how I securely connect and encrypt all communications to my home network.
Part 2, SSH
Sunday, October 7, 2007
Run a Windows application on your Mac
I decided to try out a product called Parallels the other day. I did this because I love my Macs, but I also love Quicken for Windows. I had heard about Parallels from a number of places, but figured now was the time to give it a try.
After installing it and installing Windows XP as a guest VM, I got to really see what was so special about this product.
The feature of Parallels that I really liked is called Coherence. With the Coherence feature enabled, it becomes very seamless when running a Windows application on your host OSX operating system. You no longer have to "swap" between the two operating systems. You can now have the Windows shell natively embedded into your OSX environment. For a peek at what this looks like, check out the image below.

It is really a powerful, clean way to implement better usability of the guest environment. You can even go farther with cross-launching applications between the two environments, but that just isn't something I'm all that interested in. My goal is to use Quicken for Windows on my Mac and this Parallels is a great way to do it!
The drawback... Have plenty of physical memory. The Mac Mini that I was running this on has 1G of memory and that was just not quite enough for a pleasurable VM experience. Swapping back and forth between the guest environment and the host environment was very noticeable and almost unusable. I'm very familiar with VM technology, both at home and at work, so I'm confident that this was not a problem with Parallels. It just takes more then 512M of memory for each operating system (the guest and the host) to run smoothly, and any VM product has to deal with this.
After installing it and installing Windows XP as a guest VM, I got to really see what was so special about this product.
The feature of Parallels that I really liked is called Coherence. With the Coherence feature enabled, it becomes very seamless when running a Windows application on your host OSX operating system. You no longer have to "swap" between the two operating systems. You can now have the Windows shell natively embedded into your OSX environment. For a peek at what this looks like, check out the image below.

It is really a powerful, clean way to implement better usability of the guest environment. You can even go farther with cross-launching applications between the two environments, but that just isn't something I'm all that interested in. My goal is to use Quicken for Windows on my Mac and this Parallels is a great way to do it!
The drawback... Have plenty of physical memory. The Mac Mini that I was running this on has 1G of memory and that was just not quite enough for a pleasurable VM experience. Swapping back and forth between the guest environment and the host environment was very noticeable and almost unusable. I'm very familiar with VM technology, both at home and at work, so I'm confident that this was not a problem with Parallels. It just takes more then 512M of memory for each operating system (the guest and the host) to run smoothly, and any VM product has to deal with this.
Monday, October 1, 2007
Backup Gmail Data
I ran across an interesting post the other day about making a backup of your email that is hosted by Google. The original author did a good job with instructions, so I won't repeat them here. I will note that I needed to a couple of things differently to make this work on my Mac.
First of all, fetchmail was already available on my Mac. (Don't you just love that OSX is really Unix? I do.)
Secondly, when configuring the .fetchmailrc file, I added a couple of things:
Okay, so my .fetchmailrc file looks like this now:
Upon running fetchmail, it downloads a few hundred messages at a time. My Gmail currently has about 1800 messages, so this will take a while to download, but that's fine. My intent here was to get a copy of my mail on my own hard drive just in case my relationship with Google ever fell through. I'll schedule this nightly via cron and in a week or two, I'll have a copy of everything.
First of all, fetchmail was already available on my Mac. (Don't you just love that OSX is really Unix? I do.)
Secondly, when configuring the .fetchmailrc file, I added a couple of things:
- and wants mda "/usr/bin/procmail -d %T" - The default behavior of fetchmail is to try and forward the mail that it downloaded to your systems SMTP service. In my case, I had never intended for my desktop machine to receive mail directly, so this was not enabled. The first time I ran fetchmail, it choked and died at this step. By adding the "mda" option, you direct fetchmail to deliver the mail locally to your default system mailbox. This will be a file that matches your username in the /var/mail directory. You can view it with a texteditor or by using the command 'mail' when you are in the Terminal.
- keep - I added this keep option so that I don't need to use the "-k" option when running the fetchmail command. Not sure why the original author didn't do this.
Okay, so my .fetchmailrc file looks like this now:
poll pop.gmail.com with proto POP3 and options no dns
user 'you@gmail.com' there with password 'itsasecret' is 'YourOSXUsername' here and wants mda "/usr/bin/procmail -d %T" options ssl keep
Upon running fetchmail, it downloads a few hundred messages at a time. My Gmail currently has about 1800 messages, so this will take a while to download, but that's fine. My intent here was to get a copy of my mail on my own hard drive just in case my relationship with Google ever fell through. I'll schedule this nightly via cron and in a week or two, I'll have a copy of everything.
Thursday, September 13, 2007
Wading through the onslaught of RSS feeds
If you don't know what a RSS feed is, you should. (I'll wait while you follow the link and read up on it.)
Okay, so now you know what RSS means, but why is it such a big deal? For me, RSS is rapidly becoming the tool that I use to keep up on all the latest information. Whether it is news, new products, weather, or tips on how to save money, RSS feeds are what I read. By subscribing (at no cost) to RSS feeds, I am able to load up a single page in my browser and view new content from a multitude of websites. This is an incredible timesaver as I no longer have to actually go out and visit each website every day. I don't have to bookmark all of those sites, nor do I have to sit through a bunch of graphic-intensive ads as each website loads into my browser.
As I wander through the Internet each day, I invariably stumble across content that I like and may want to read more about in the future. When this happens, I look for a feed that I can subscribe to. If you are a Firefox or Safari user, the existence of a feed will be highlighted for you in the address bar of your browser. If not, just scan the page for words "subscribe", "rss", or "feed". You can also look for a little orange icon somewhere that is the accepted symbol for RSS feed.
Once you choose to subscribe to a feed, then you will need an application known as a "feed reader" or "aggregator". You can find lots of them out there, but I would recommend Google Reader as a good place to start. It's easy to use and accessible from whatever computer you happen to be on.
As you start collecting a few feeds, you will invariably come across one that has "high traffic". This means that they post new content many times throughout the day. This can be overwhelming if you have many feeds to browse or if you haven't checked your feeds for a few days.
I have recently ran across a tool that helps with this problem. It is called aideRSS. This is a great tool and even comes with a nice training video that shows you how to use their site. By using this tool, you will be able to add a filtered feed to your reader instead of the original one that you were interested in. This allows you to only spend time reading content that aideRSS has noted as popular.
The main drawback of this approach is that you won't be the "first" to read the new content and/or comment on it. If that is important to you, then you should retain the original feed subscription. For me, personally, I am content with a delay before I see the content when it means that I'm going to be viewing content that the community has already voted as popular.
Take a few moments, check out aideRSS, and let me know how it goes.
Okay, so now you know what RSS means, but why is it such a big deal? For me, RSS is rapidly becoming the tool that I use to keep up on all the latest information. Whether it is news, new products, weather, or tips on how to save money, RSS feeds are what I read. By subscribing (at no cost) to RSS feeds, I am able to load up a single page in my browser and view new content from a multitude of websites. This is an incredible timesaver as I no longer have to actually go out and visit each website every day. I don't have to bookmark all of those sites, nor do I have to sit through a bunch of graphic-intensive ads as each website loads into my browser.
As I wander through the Internet each day, I invariably stumble across content that I like and may want to read more about in the future. When this happens, I look for a feed that I can subscribe to. If you are a Firefox or Safari user, the existence of a feed will be highlighted for you in the address bar of your browser. If not, just scan the page for words "subscribe", "rss", or "feed". You can also look for a little orange icon somewhere that is the accepted symbol for RSS feed.
Once you choose to subscribe to a feed, then you will need an application known as a "feed reader" or "aggregator". You can find lots of them out there, but I would recommend Google Reader as a good place to start. It's easy to use and accessible from whatever computer you happen to be on.
As you start collecting a few feeds, you will invariably come across one that has "high traffic". This means that they post new content many times throughout the day. This can be overwhelming if you have many feeds to browse or if you haven't checked your feeds for a few days.
I have recently ran across a tool that helps with this problem. It is called aideRSS. This is a great tool and even comes with a nice training video that shows you how to use their site. By using this tool, you will be able to add a filtered feed to your reader instead of the original one that you were interested in. This allows you to only spend time reading content that aideRSS has noted as popular.
The main drawback of this approach is that you won't be the "first" to read the new content and/or comment on it. If that is important to you, then you should retain the original feed subscription. For me, personally, I am content with a delay before I see the content when it means that I'm going to be viewing content that the community has already voted as popular.
Take a few moments, check out aideRSS, and let me know how it goes.
Saturday, September 1, 2007
Switching Cell Phone Providers, pt 5 (Customer Service)
The last aspect of this whole evaluation I wanted to look at was their customer service. I have heard raves about Tmobile's customer service. I have called them a total of two times so far. They are certainly the friendliest company that I have dealt with. I was very impressed.
My second call to Customer service was to actually port my Cingular number over to my Tmobile account. After getting through the ARU, I spoke to the initial operator who validated my info and then transferred me to a more technical staff member for the number porting. He walked me through each and every step and about how long it would take. My expectations are well set (should be all done by tomorrow) and I'm ready to go.
At this point, I would have to concur with others that I've read from and talked to. Tmobile's customer service really is great!
My second call to Customer service was to actually port my Cingular number over to my Tmobile account. After getting through the ARU, I spoke to the initial operator who validated my info and then transferred me to a more technical staff member for the number porting. He walked me through each and every step and about how long it would take. My expectations are well set (should be all done by tomorrow) and I'm ready to go.
At this point, I would have to concur with others that I've read from and talked to. Tmobile's customer service really is great!
Saturday, August 25, 2007
Switching Cell Phone Providers, pt 4 (Website)
Next test, the website. I wanted to see how easy it was to navigate and manage my account. The other thing that I really needed to know was how I could manage my 5 numbers.
Anyway, since I am using a non-"faves" enabled phone, I wanted to see if I could manage my list of 5 numbers through the website. Sure enough, I can and did. That question answered.
The other thing that I liked about the website is that it shows you how many minutes you've consumed for the month. Unfortunately, it doesn't appear to give detailed information on call data. Perhaps, it will after a monthly statement is generated.
Part 3, Plan | Part 5, Customer Service
Anyway, since I am using a non-"faves" enabled phone, I wanted to see if I could manage my list of 5 numbers through the website. Sure enough, I can and did. That question answered.
The other thing that I liked about the website is that it shows you how many minutes you've consumed for the month. Unfortunately, it doesn't appear to give detailed information on call data. Perhaps, it will after a monthly statement is generated.
Part 3, Plan | Part 5, Customer Service
Saturday, August 18, 2007
Switching Cell Phone Providers, pt 3 (Plan)
Before I started searching for a plan, I needed to know what type of usage I would need. I was abler to pull my last 6 months of usage records from my current Cingular account. A quick analysis showed that I used about 400 minutes a month and sent/received 110 SMS messages. Turns out I was buying a lot more then I was using.
I got signed up on the base "myFaves" plan with Tmobile. This plan offers unlimited (again, within context) calling to 5 numbers. For all other numbers, 300 minutes.
I now have a Tmobile plan with a temporary number. At least, that is what they called it. I had told them when signing up that I would either cancel the plan or roll my existing Cingular number over. I got the phone home and immediately removed the SIM card and plugged it into my existing phone. Ah, the beauty of GSM... I already own a SLVR which I really like. The free phone that came with the plan was a nice, pink Miami Ink RAZR. Needless to say, that's just not my style.
Anyway, 5 minutes after I got home, my existing SLVR was up and running on Tmobile's network. By the way, the perfect way to evaluate two services is to actually use the exact same device. The Mythbusters would be proud of me. I immediately phoned a friend and walked through the house to see what the service was like. First impression was good. I definitely have some dead spots in the house on Cingular's network. Now, does this alone mean that Tmobile is better then Cingular? Not really, it just means that there is likely a Tmobile tower closer to my house then a Cingular tower.
Over the next week, I continued to check the bars on my phone (which isn't foolproof) and called friends and family from different locations. Overall, in my area, I got just as good, if not better, service with Tmobile then with Cingular. That aspect of my evaluation is looking good.
Part 2, Coverage | Part 4, Website
I got signed up on the base "myFaves" plan with Tmobile. This plan offers unlimited (again, within context) calling to 5 numbers. For all other numbers, 300 minutes.
I now have a Tmobile plan with a temporary number. At least, that is what they called it. I had told them when signing up that I would either cancel the plan or roll my existing Cingular number over. I got the phone home and immediately removed the SIM card and plugged it into my existing phone. Ah, the beauty of GSM... I already own a SLVR which I really like. The free phone that came with the plan was a nice, pink Miami Ink RAZR. Needless to say, that's just not my style.
Anyway, 5 minutes after I got home, my existing SLVR was up and running on Tmobile's network. By the way, the perfect way to evaluate two services is to actually use the exact same device. The Mythbusters would be proud of me. I immediately phoned a friend and walked through the house to see what the service was like. First impression was good. I definitely have some dead spots in the house on Cingular's network. Now, does this alone mean that Tmobile is better then Cingular? Not really, it just means that there is likely a Tmobile tower closer to my house then a Cingular tower.
Over the next week, I continued to check the bars on my phone (which isn't foolproof) and called friends and family from different locations. Overall, in my area, I got just as good, if not better, service with Tmobile then with Cingular. That aspect of my evaluation is looking good.
Part 2, Coverage | Part 4, Website
Saturday, August 11, 2007
4 Things To Think About If You Must Use WEP
Okay, if you've read my previous posts, know how to use WPA to secure your wireless network. For some, this will not be an option. If you absolutely must use WEP, let me give you a few things to keep in mind.
#1) Use the longest password possible. At least 128 bit. This won't buy you much security, but it will mean that someone looking to crack your password will have to sniff more traffic. This means they have to be connected for a longer period of time before being able to discover your password.
#2) Disconnect the devices connected to your wireless network when they aren't in use. If you have a computer that you leave on all the time, it is constantly "checking in" with your access point. This conversational traffic is exactly what a malicious person needs in order to collect the right information to crack your password. If you are like me, you don't like powering down your equipment every day. In this case, just access your wireless configuration on your laptop and disable the connection. When you are ready to use it again, just enable it. Easy.
#3) Use a firewall. If you don't know what this is or how to configure it, don't worry. There are lots of resources available on the 'net. I may also do a basic writeup on it if there is interest. Basically, you want to keep your wireless network separate from the rest of your home network that has your other computers on it. If someone were to access your wireless network, you don't want them getting to your internal resources.
#4) Be smart about the type of data that you transfer over your wireless network. Assume that some stranger is going to get a copy of it and ask yourself if it is something that needs to be more private. Is it something that you would write on a postcard and send through the post office? If so, it's probably okay for use on your wireless network.
#1) Use the longest password possible. At least 128 bit. This won't buy you much security, but it will mean that someone looking to crack your password will have to sniff more traffic. This means they have to be connected for a longer period of time before being able to discover your password.
#2) Disconnect the devices connected to your wireless network when they aren't in use. If you have a computer that you leave on all the time, it is constantly "checking in" with your access point. This conversational traffic is exactly what a malicious person needs in order to collect the right information to crack your password. If you are like me, you don't like powering down your equipment every day. In this case, just access your wireless configuration on your laptop and disable the connection. When you are ready to use it again, just enable it. Easy.
#3) Use a firewall. If you don't know what this is or how to configure it, don't worry. There are lots of resources available on the 'net. I may also do a basic writeup on it if there is interest. Basically, you want to keep your wireless network separate from the rest of your home network that has your other computers on it. If someone were to access your wireless network, you don't want them getting to your internal resources.
#4) Be smart about the type of data that you transfer over your wireless network. Assume that some stranger is going to get a copy of it and ask yourself if it is something that needs to be more private. Is it something that you would write on a postcard and send through the post office? If so, it's probably okay for use on your wireless network.
Thursday, August 2, 2007
Use WPA instead of WEP, pt 2
Lesson #2) Fine. I'll use the instruction manual. What should I be looking to do? Great! Look for instructions on how to connect to the administration function of the device you are setting up. This will usually be accessible on a private address in the 192.168. range. This means that you plug it in and then use your browser to access a special address that is given to you in the instruction manual. Once you have accessed this function, you should be looking for a security section. This will give you options on what kind of wireless security you want. At the time of this writing, most devices give you three options: open, WEP, and WPA. You want to choose WPA. (Specifically, referring to Pre-Shared Key or "Personal". The Enterprise level is not within the scope of this blog.)
The setup of WPA is really not any more difficult then WEP. Which is what makes it frustrating for me to see people still using WEP. There are probably a handful of situations in which folks may still want to use WEP. Most of these being to support older equipment that was purchased before the WPA protocol was developed. We will cover approaches to using WEP safely later.
Lesson #3) Choose a good password. Good passwords are difficult for humans. They are hard to remember, hard to come up with, hard to type. This is unfortunate and typically leads most people to choosing bad passwords. Bad passwords are short and easy to remember. They are things that can be found in dictionaries or on your myspace page (birthday, dog's name, friend's name, etc). When thinking about a good password for your wireless network, you have one thing going for you; you just don't have to type it very often, if ever. Most modern devices allow you to enter the password one time and it will retain it.
When choosing a password, you want to make it as long as possible and as random as possible. WPA allows for a password of up to 64 hexidecimal characters. I know what you're thinking, how am I going to type in a 64 character password? Don't worry, I will walk you through the approach that I use in a bit. You won't have to type a thing. The point here is that you want the longest password possible. It doesn't make any difference on your day-to-day computer use, but it does increase the time needed for a malicious person to gain access to your network.
Now, to get a random password, you need a thing called a "password generator". With OS X, you can create one using the Keychain application. If you are a Firefox user, there is an excellent extension available called SecurePassword. If neither of these are an option for you, there are a few of them available on the web. My favorite website for this is GRC. GRC's password generator will build the perfect password for WPA merely by accessing the link above. They provide a 64 character hexidecimal password along with a 63 character alpha-numeric one. Either one will work for WPA, so let's choose the alpha-numeric one since it is more human-friendly. When I accessed the site, this is the password that I received:
lKAg0kImzxZ3HdDrlojUaUCXfInGNBXbMai4V7Afz2uh9nMNiByqaCfD3KMXqlD
Don't let this scare you. Just highlight it and copy it into your computer's buffer (ctrl+c or Cmd+c). Open up a text editor and paste (ctrl+v or Cmd+v) it into the text editor. Do a quick File|Save and you've got your password (and you didn't have to type a thing). Now, back to the wireless device we were configuring... You've selected WPA and are prompted to enter the password or the "pre shared key". Just switch back to your text editor, copy your random password, and paste it into the password field. Now, look for the save button and you are done with your access point configuration! Once you hit save, your device will probably restart and anyone currently connected to it will be dropped. They will also not be able to re-connect without your new random password.
Lesson #4) Configure only the computers that you want on your wireless network. Your next challenge is how to get that new password to your laptop so that it can access your wireless network. There are, of course, a number of ways in which to do this. The one that I propose is called the sneakernet. Put on your tin foil hat with me and find a blank disk or USB thumb drive. This password isn't something that you want to leave on your computer, transfer to your friend via email, or post on a website. Ever. You must maintain strict control over this password. Find a disk... floppy, CD, DVD, ZIP, whatever. My preference is CD these days. You want something that will be accessible to most types of computers. Remember that file you created with your text editor? Move it to the disk.
Now, take the disk and insert it into the laptop you want to access your wireless network. Open up the text file, highlight the password, and copy it into your buffer. Now, open up your computers wireless configuration and find your network in the list. Hopefully, it will say "secured" or something to that effect. When you select it, it will prompt for a password. No problem! You just paste the new password into the both fields and you're done. If done correctly, your laptop is now authenticated to your wireless network and you are all set. Just take out the disk and repeat the procedure on any other computers that you want to have connected to your wireless network. Friend of yours is visiting and wants to get their email? Hand them the disk. Just make sure you get it back. :)
The setup of WPA is really not any more difficult then WEP. Which is what makes it frustrating for me to see people still using WEP. There are probably a handful of situations in which folks may still want to use WEP. Most of these being to support older equipment that was purchased before the WPA protocol was developed. We will cover approaches to using WEP safely later.
Lesson #3) Choose a good password. Good passwords are difficult for humans. They are hard to remember, hard to come up with, hard to type. This is unfortunate and typically leads most people to choosing bad passwords. Bad passwords are short and easy to remember. They are things that can be found in dictionaries or on your myspace page (birthday, dog's name, friend's name, etc). When thinking about a good password for your wireless network, you have one thing going for you; you just don't have to type it very often, if ever. Most modern devices allow you to enter the password one time and it will retain it.
When choosing a password, you want to make it as long as possible and as random as possible. WPA allows for a password of up to 64 hexidecimal characters. I know what you're thinking, how am I going to type in a 64 character password? Don't worry, I will walk you through the approach that I use in a bit. You won't have to type a thing. The point here is that you want the longest password possible. It doesn't make any difference on your day-to-day computer use, but it does increase the time needed for a malicious person to gain access to your network.
Now, to get a random password, you need a thing called a "password generator". With OS X, you can create one using the Keychain application. If you are a Firefox user, there is an excellent extension available called SecurePassword. If neither of these are an option for you, there are a few of them available on the web. My favorite website for this is GRC. GRC's password generator will build the perfect password for WPA merely by accessing the link above. They provide a 64 character hexidecimal password along with a 63 character alpha-numeric one. Either one will work for WPA, so let's choose the alpha-numeric one since it is more human-friendly. When I accessed the site, this is the password that I received:
lKAg0kImzxZ3HdDrlojUaUCXfInGNBXbMai4V7Afz2uh9nMNiByqaCfD3KMXqlD
Don't let this scare you. Just highlight it and copy it into your computer's buffer (ctrl+c or Cmd+c). Open up a text editor and paste (ctrl+v or Cmd+v) it into the text editor. Do a quick File|Save and you've got your password (and you didn't have to type a thing). Now, back to the wireless device we were configuring... You've selected WPA and are prompted to enter the password or the "pre shared key". Just switch back to your text editor, copy your random password, and paste it into the password field. Now, look for the save button and you are done with your access point configuration! Once you hit save, your device will probably restart and anyone currently connected to it will be dropped. They will also not be able to re-connect without your new random password.
Lesson #4) Configure only the computers that you want on your wireless network. Your next challenge is how to get that new password to your laptop so that it can access your wireless network. There are, of course, a number of ways in which to do this. The one that I propose is called the sneakernet. Put on your tin foil hat with me and find a blank disk or USB thumb drive. This password isn't something that you want to leave on your computer, transfer to your friend via email, or post on a website. Ever. You must maintain strict control over this password. Find a disk... floppy, CD, DVD, ZIP, whatever. My preference is CD these days. You want something that will be accessible to most types of computers. Remember that file you created with your text editor? Move it to the disk.
Now, take the disk and insert it into the laptop you want to access your wireless network. Open up the text file, highlight the password, and copy it into your buffer. Now, open up your computers wireless configuration and find your network in the list. Hopefully, it will say "secured" or something to that effect. When you select it, it will prompt for a password. No problem! You just paste the new password into the both fields and you're done. If done correctly, your laptop is now authenticated to your wireless network and you are all set. Just take out the disk and repeat the procedure on any other computers that you want to have connected to your wireless network. Friend of yours is visiting and wants to get their email? Hand them the disk. Just make sure you get it back. :)
Friday, July 27, 2007
Use WPA instead of WEP
Okay, folks, it is time once again to review the state of today's wireless 802.11 (also known by the marketing term, WiFi) security. This has been documented time and time again, but it has recently became clear to me that it apparently isn't sinking in. One of my goals with this blog is to try and educate friends and family, so I thought I would write something up that is in plain English and implore you to think about your wireless situation at home.
I was recently on vacation in a small town in Idaho when I fired up my laptop and found no fewer then six wireless networks within range. A couple of things surprised me about this. The first being that there were six(!) networks in my immediate vicinity in a town with a population of 4,000. I am not used to seeing this kind of coverage in the smaller mountain towns that I've visited. The second, and probably more, surprising aspect of this was that all of them were secured! That's right, none of them were set to allow open access, nor did they have the all-too-familiar network name "linksys" or "default".
Unfortunately, they had all used WEP as the means for securing their network. This is horribly insecure and merely serves as a means to keep the honest people honest. Perhaps, that is all the owners were after, but I would like to encourage you to go a step farther in securing your own home network. It's really not that hard and will take 10-15 minutes, tops. If you haven't already, please read my post regarding the dangers of using WEP.
If you are still reading, then perhaps I've convinced you to convert your network from WEP or open to WPA. If that is the case, read on...
Lesson #1) Do not buy an access point (also known as "router", "wireless hub", or just plain "wireless"), take it home, plug it in, and just start using it. This is what we would call the "default" or open access. It comes with an instruction manual for a reason. Use it! :)
Next Lessons...
I was recently on vacation in a small town in Idaho when I fired up my laptop and found no fewer then six wireless networks within range. A couple of things surprised me about this. The first being that there were six(!) networks in my immediate vicinity in a town with a population of 4,000. I am not used to seeing this kind of coverage in the smaller mountain towns that I've visited. The second, and probably more, surprising aspect of this was that all of them were secured! That's right, none of them were set to allow open access, nor did they have the all-too-familiar network name "linksys" or "default".
Unfortunately, they had all used WEP as the means for securing their network. This is horribly insecure and merely serves as a means to keep the honest people honest. Perhaps, that is all the owners were after, but I would like to encourage you to go a step farther in securing your own home network. It's really not that hard and will take 10-15 minutes, tops. If you haven't already, please read my post regarding the dangers of using WEP.
If you are still reading, then perhaps I've convinced you to convert your network from WEP or open to WPA. If that is the case, read on...
Lesson #1) Do not buy an access point (also known as "router", "wireless hub", or just plain "wireless"), take it home, plug it in, and just start using it. This is what we would call the "default" or open access. It comes with an instruction manual for a reason. Use it! :)
Next Lessons...
Friday, July 20, 2007
Why WEP Should Be Considered Bad Form
If you have a wireless network at home and you've either left it open (unsecured) or you have secured it using the WEP option, this article is for you. If you have wireless and you have no idea what the preceding sentence means, you need to read this and my follow-up entries on how to secure your wireless network.
If you think WEP is good enough for your wireless security, let me educate you on how incredibly simple it is to bypass. One would need the correct hardware (an Atheros based wireless card - $50), the correct software (available over the Internet - free), and be near enough to your wireless network to pick up a signal (also free). Once all three of these are in place, it takes less then an hour (in some cases, far less!) to come up with the password that you used to supposedly secure your network. At this point, they are on your network. Mostly, they will just be interested in accessing the Internet for free. Mostly. If this doesn't scare you, it should. If you have other computers on your home network that have your financial information on them, this should scare you very much. Kudos to you for choosing to secure your network instead of using the default "open" network. Unfortunately, using WEP isn't much better then just leaving your network open.
Perhaps you are one that doesn't care if someone else uses your network to access the Internet? While that is altruistic and very generous of you, it does leave you open to risks. For starters, most ISPs specifically forbid the sharing of your home Internet service in their terms of service. You can argue how the "Man" is trying to squeeze more money out of us all by doing this and you'd likely be right. But that doesn't stop them from disconnecting you if they feel that you've infringed on the agreement that you submitted to when purchasing their service. Furthermore, these types of companies believe that is a violation of federal or state laws and may seek action against you.
If the risk of the Man disconnecting you isn't enough, think about what kinds of bad things can be done online and will be traced back to your home address. Accessing child porn, probing government networks, and communicating with known terrorists are all things that will raise flags with your federal government and your ISP. From what I've read, it is a legal grey area on whether or not you could be held liable for this. (How believable is your defense of "It wasn't me. Someone must have used my wireless network.") Is it worth the hassle?
Now, I'm really not the doom and gloom type. The chances of this happening to you are small, but not impossible. If you live in a sparsely populated area, the chances of one of your neighbors wanting to break into your network to conduct malicious activity are slim. If it isn't one of your neighbors, but a stranger instead, then ideally you'd notice a car sitting out on your street with a person inside using a laptop. If you live in a larger city or a densely populated area, there are many more people available and interested in using your network. If you are in an apartment building, you would never even see that this is happening.
http://news.com.com/2100-1039-5112000.html
http://money.cnn.com/2005/08/08/technology/personaltech/internet_piracy/?cnn=yes
http://www.pcworld.com/article/id,122153-page,1/article.html
If you think WEP is good enough for your wireless security, let me educate you on how incredibly simple it is to bypass. One would need the correct hardware (an Atheros based wireless card - $50), the correct software (available over the Internet - free), and be near enough to your wireless network to pick up a signal (also free). Once all three of these are in place, it takes less then an hour (in some cases, far less!) to come up with the password that you used to supposedly secure your network. At this point, they are on your network. Mostly, they will just be interested in accessing the Internet for free. Mostly. If this doesn't scare you, it should. If you have other computers on your home network that have your financial information on them, this should scare you very much. Kudos to you for choosing to secure your network instead of using the default "open" network. Unfortunately, using WEP isn't much better then just leaving your network open.
Perhaps you are one that doesn't care if someone else uses your network to access the Internet? While that is altruistic and very generous of you, it does leave you open to risks. For starters, most ISPs specifically forbid the sharing of your home Internet service in their terms of service. You can argue how the "Man" is trying to squeeze more money out of us all by doing this and you'd likely be right. But that doesn't stop them from disconnecting you if they feel that you've infringed on the agreement that you submitted to when purchasing their service. Furthermore, these types of companies believe that is a violation of federal or state laws and may seek action against you.
If the risk of the Man disconnecting you isn't enough, think about what kinds of bad things can be done online and will be traced back to your home address. Accessing child porn, probing government networks, and communicating with known terrorists are all things that will raise flags with your federal government and your ISP. From what I've read, it is a legal grey area on whether or not you could be held liable for this. (How believable is your defense of "It wasn't me. Someone must have used my wireless network.") Is it worth the hassle?
Now, I'm really not the doom and gloom type. The chances of this happening to you are small, but not impossible. If you live in a sparsely populated area, the chances of one of your neighbors wanting to break into your network to conduct malicious activity are slim. If it isn't one of your neighbors, but a stranger instead, then ideally you'd notice a car sitting out on your street with a person inside using a laptop. If you live in a larger city or a densely populated area, there are many more people available and interested in using your network. If you are in an apartment building, you would never even see that this is happening.
http://news.com.com/2100-1039-5112000.html
http://money.cnn.com/2005/08/08/technology/personaltech/internet_piracy/?cnn=yes
http://www.pcworld.com/article/id,122153-page,1/article.html
Monday, July 16, 2007
Switching Cell Phone Providers, pt 2 (Coverage)
Okay, so I start researching Tmobile. First off, I need to learn about their coverage. I check out their website to see if they have a coverage map. I was impressed on two fronts. First of all, they offer a method to search on an address basis, so that you can drill down exactly. Secondly, they offer a view of how strong the signal is, not just whether or not there is one. I found this encouraging even if I might have a lower signal on a particular search. I like it when companies are just upfront about things.
My next dilemma is figuring out how to test the service without getting locked into a contract. (side note: I hate the fact that every company out there wants to lock you into a two year contract.) A friend of mine pointed me to Costco. Probably wouldn't have occurred to me to check there, but I swung by after work one day to take a look. They have a small kiosk where they offer phones and plans from multiple providers. The really cool thing about this is that they have worked out some deal with each provider where you have two weeks to change your mind and get out of the contract. This was my perfect solution!
Part 1, Intro | Part 3, Plan
My next dilemma is figuring out how to test the service without getting locked into a contract. (side note: I hate the fact that every company out there wants to lock you into a two year contract.) A friend of mine pointed me to Costco. Probably wouldn't have occurred to me to check there, but I swung by after work one day to take a look. They have a small kiosk where they offer phones and plans from multiple providers. The really cool thing about this is that they have worked out some deal with each provider where you have two weeks to change your mind and get out of the contract. This was my perfect solution!
Part 1, Intro | Part 3, Plan
Thursday, July 12, 2007
Switching Cell Phone Providers
I've been a customer of Cingular since the first time they were AT&T. I'm not particularly fond of the company, nor the service. What I do like is GSM and the cooler phones that are available for that platform. Well, in the US, if you want GSM, it's Cingular or Tmobile. I'd always been just satisfied enough with Cingular that I'd never bothered changing providers.
Well, that has now changed. It started a few weeks ago with a desire on my part to save some money and reduce a family plan with two lines down to just one line. I've also been doing more with SMS lately. Not so much to chat with friends, but more to use Google Calendar and Search. The one thing that I do like about Cingular is the number of retail stores in my area. I much prefer talking to someone face to face over sitting on hold with a call center.
Actually, I take that back, I would rather do these kinds of things online through the website, but I have just never had a good website experience with companies like Cingular, Qwest, or DirecTv when it comes to moves/adds/changes. So, long story short, I go into the Cingular store and am told that they cannot remove lines from a family plan. Yes, if I wanted to add a line, they can do it, but they cannot remove. Um... Okay, next question. I see a sign on the wall that says "Unlimited Text Messaging - $4.99". That sounds good to me, how about we add that? Well, turns out that Cingular has redefined the word "unlimited". In this particular context, it means unlimited messages to limited numbers. With my desire to use Google services, this doesn't help me. If I want true unlimited, it costs $19.99/month. Sorry, just too much money for me. I leave the store without making any changes, but determined to learn more about Tmobile.

Part 2, Coverage
Well, that has now changed. It started a few weeks ago with a desire on my part to save some money and reduce a family plan with two lines down to just one line. I've also been doing more with SMS lately. Not so much to chat with friends, but more to use Google Calendar and Search. The one thing that I do like about Cingular is the number of retail stores in my area. I much prefer talking to someone face to face over sitting on hold with a call center.
Actually, I take that back, I would rather do these kinds of things online through the website, but I have just never had a good website experience with companies like Cingular, Qwest, or DirecTv when it comes to moves/adds/changes. So, long story short, I go into the Cingular store and am told that they cannot remove lines from a family plan. Yes, if I wanted to add a line, they can do it, but they cannot remove. Um... Okay, next question. I see a sign on the wall that says "Unlimited Text Messaging - $4.99". That sounds good to me, how about we add that? Well, turns out that Cingular has redefined the word "unlimited". In this particular context, it means unlimited messages to limited numbers. With my desire to use Google services, this doesn't help me. If I want true unlimited, it costs $19.99/month. Sorry, just too much money for me. I leave the store without making any changes, but determined to learn more about Tmobile.

Part 2, Coverage
Saturday, July 7, 2007
OpenDNS
Ran across a service this week called OpenDNS. Basically, they offer to resolve names for anyone who cares to point to them. Pure and simple. That's just for starters though... They have done some really nifty tricks that I haven't seen done before in the DNS layer.
- They can fix basic typos in the web address of your browser. Yep, if you happen to screw up ".com" or ".org", the service will take a guess and redirect you to the most obvious root domain. I haven't yet tested the extent of this, but it is a clever trick. Yeah, it's not revolutionary, but still, it saves a few seconds.
- They claim to block phishing sites. This is probably a good thing, but frankly just not something I really need. If you're reading this and you, for some insane reason, click on any link that is sent to your email, then yes, you want phishing sites blocked. I wasn't able to determine from their website where they get the list of known phishing sites. My hunch is that it could be stale at any given point in time.
- They also block adult websites. This is historically a difficult thing to do as these websites come and go very quickly. It looks like OpenDNS has partnered with another company that reviews websites and maintains a blacklist. The really interesting thing about this feature is doing it with DNS. No proxy software to install only to have the teenagers work around it. No web filtering crap that tries to load into your browser. It's just simple and clean. An enterprising youth could likely still get where they wanted to go by running through a proxy server that isn't resolving against OpenDNS, but at least this keeps the honest kids honest.
- They do some other tricks with hostname redirection to provide the ability to do "shortcuts" in your web browser. Some may find this useful. I, personally, do not. Sites that I frequent enough to need a shortcut seem to find themselves in my Firefox history so I rarely type a full URL anyway.
Subscribe to:
Posts (Atom)



